Blocking ads and malware with a doctored hosts file
by William Jackson on 2010-03-08
NOTE: When I use the method described here, Forefront Endpoint Protection 2010 repeatedly detects SettingsModifier:Win32/PossibleHostsFileHijack on the client.
Replacing the default hosts file is a great way to block ads and malware while browsing the Internet. An oft-updated malware-blocking hosts file, along with instructions for how to use it, can be found on this great Windows troubleshooting website.
Deploying the doctored hosts file on a single computer is elementary. Deploying the doctored hosts file to several hundred managed systems is much more fun and rewarding. It is also rather easy, thanks to Group Policy Preferences. Hereʼs how you do it:
In Group Policy Management Editor, browse down to Computer Configuration\Preferences\Windows Settings\Files.
Right-click on Files and choose New → File. Set the Action to Replace (Update does not work, because it will not overwrite a file that already exists; it will only change attributes). Set the Source file(s) to %gptpath%\\files\\hosts and the Destination File to %systemdir%\\drivers\\etc\\hosts. Check the Archive Attribute, but leave everything else unchecked.
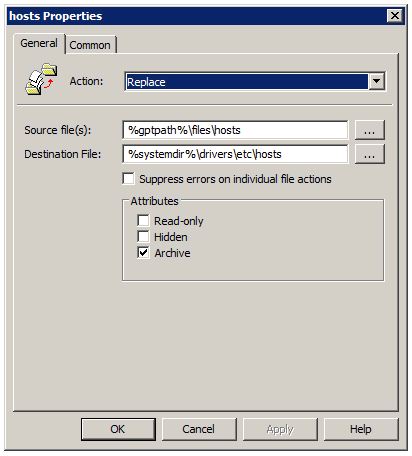
%gptpath% is a magic little variable that resolves to a folder in SYSVOL where all the settings for this Group Policy Object are saved. In this case, it will resolve to ...\\Policies\\{gpo-unique-id}\\Machine. Inside that folder you should already see two more folders: Preferences and Scripts. Create a new folder called Files and put the hosts file you downloaded from the previously-linked website in the Files folder.
In truth, you can put the source file anywhere, and modify the GPO accordingly, but I put it in this particular folder so I donʼt have to mess with NTFS permissions on the source file. If a computer can read the Group Policy Object, then it will be able to read everything in these folders in SYSVOL. Unless you go and explicitly change permissions on your source file. Now why would you do a thing like that?
Now save the GPO and test it out. Once you are convinced it works as advertised and doesnʼt mess up your environment, link it wherever you want. Now sleep a little better at night.
Donʼt forget to check the previously-linked website periodically for new versions of the hosts file.